URL Tampering is a real security threat. In this short, I will summarize what APEX Session State Protection (SSP) is, discuss how it protects us from URL tampering and give my recommendations on best practices. If you follow these recommendations, your Oracle APEX applications will be protected from URL tampering.
How Session State Protection Works
Without SSP, it would be possible to change the values of application and page items from the browser address bar. If you have SSP enabled for page items, APEX will calculate a checksum (cs=) for the enabled item values and append the checksum to the end of the URL e.g.
https://example.com/pls/apex/r/jdd/test-ssp/home?p1_customer_id=66777&session=10780717456906&cs=3uWtJONhMNcTUc69h6Fr2kWnZTPzt0WWRjAqtbV5N56Mdrih5AiXSOHHVH-2smO9ykPI3CP-X3A3d8oEiRedg8Q
When the page is submitted, APEX re-calculates the checksum on the item values and compares it to the original checksum to ensure the item values were not changed maliciously. The user will get a 'Session state protection violation' error message if the checksums differ.
Where is SSP Configured?
SSP can be configured in four places: Application, Page, Page Item, and Application Item.
Application (Session State Protection)
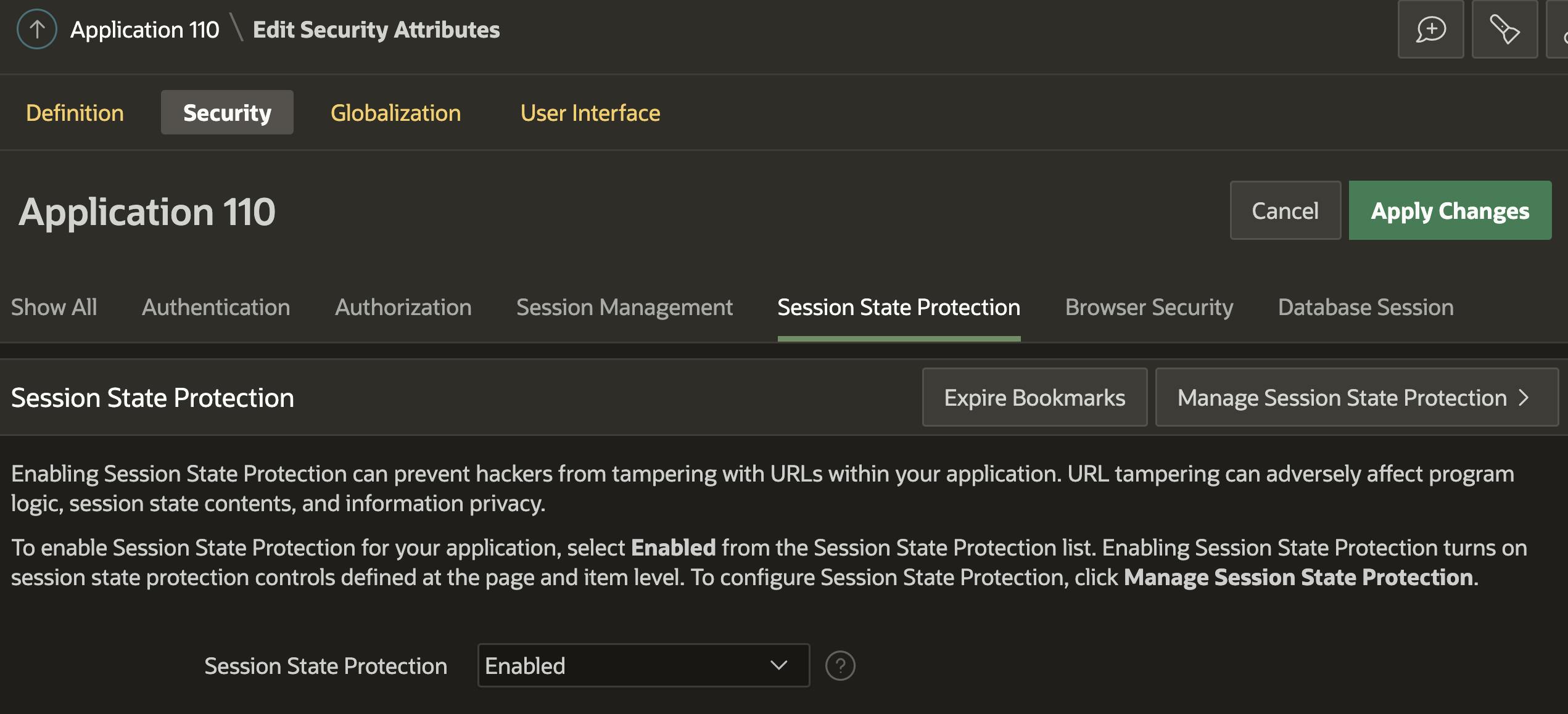 If you disable SSP at the Application Level, all other page, page item, and application item SSP settings will be ignored.
If you disable SSP at the Application Level, all other page, page item, and application item SSP settings will be ignored.
Recommendation
Always Enable Application Session State Protection. Always!
Page (Page Access Protection)
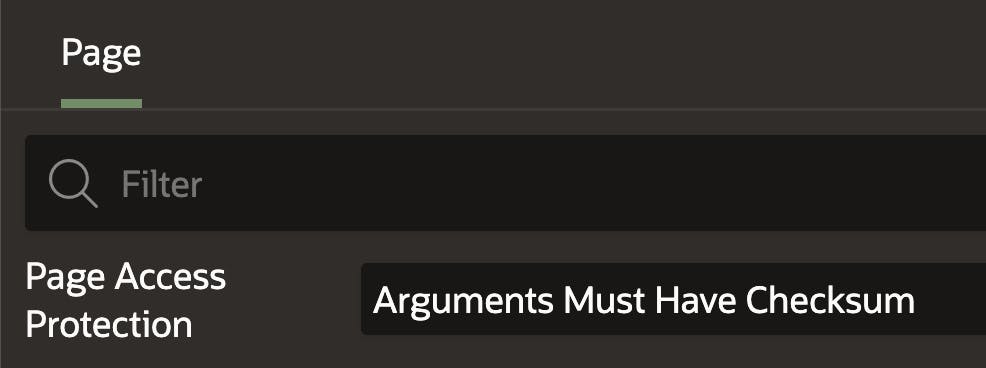 Enabling Page Access Protection prevents users from tampering with the URL while on that page. It does not prevent users on other pages from tampering with items on a page with Page Access Protection enabled. For example, if you enable Page Access Protection for page 15 but have it disabled for page 14, then a user on page 14 could still tamper with items on page 15 but not the other way around. You only must forget to set this on one page, and it opens up every item on every other page to attack.
Enabling Page Access Protection prevents users from tampering with the URL while on that page. It does not prevent users on other pages from tampering with items on a page with Page Access Protection enabled. For example, if you enable Page Access Protection for page 15 but have it disabled for page 14, then a user on page 14 could still tamper with items on page 15 but not the other way around. You only must forget to set this on one page, and it opens up every item on every other page to attack.
Recommendation
Never set Page Access Protection to 'Unrestricted'. Any other options are fine, but you will typically use 'Arguments Must Have Checksum'.
Page Item (Session State Protection)
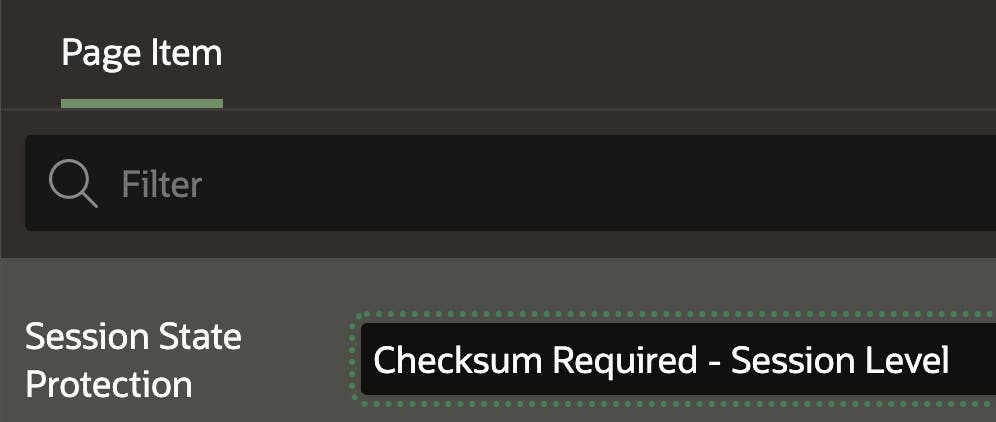 Page Item SSP may be the most important. You are protected if SSP is set for your application, and you have SSP enabled for every single page item. This is regardless of whether Page Access Protection is enabled.
Page Item SSP may be the most important. You are protected if SSP is set for your application, and you have SSP enabled for every single page item. This is regardless of whether Page Access Protection is enabled.
Recommendation
Set Page Item (Session State Protection) to 'Checksum Required - Session Level' unless you have a specific reason not to.
Application Item
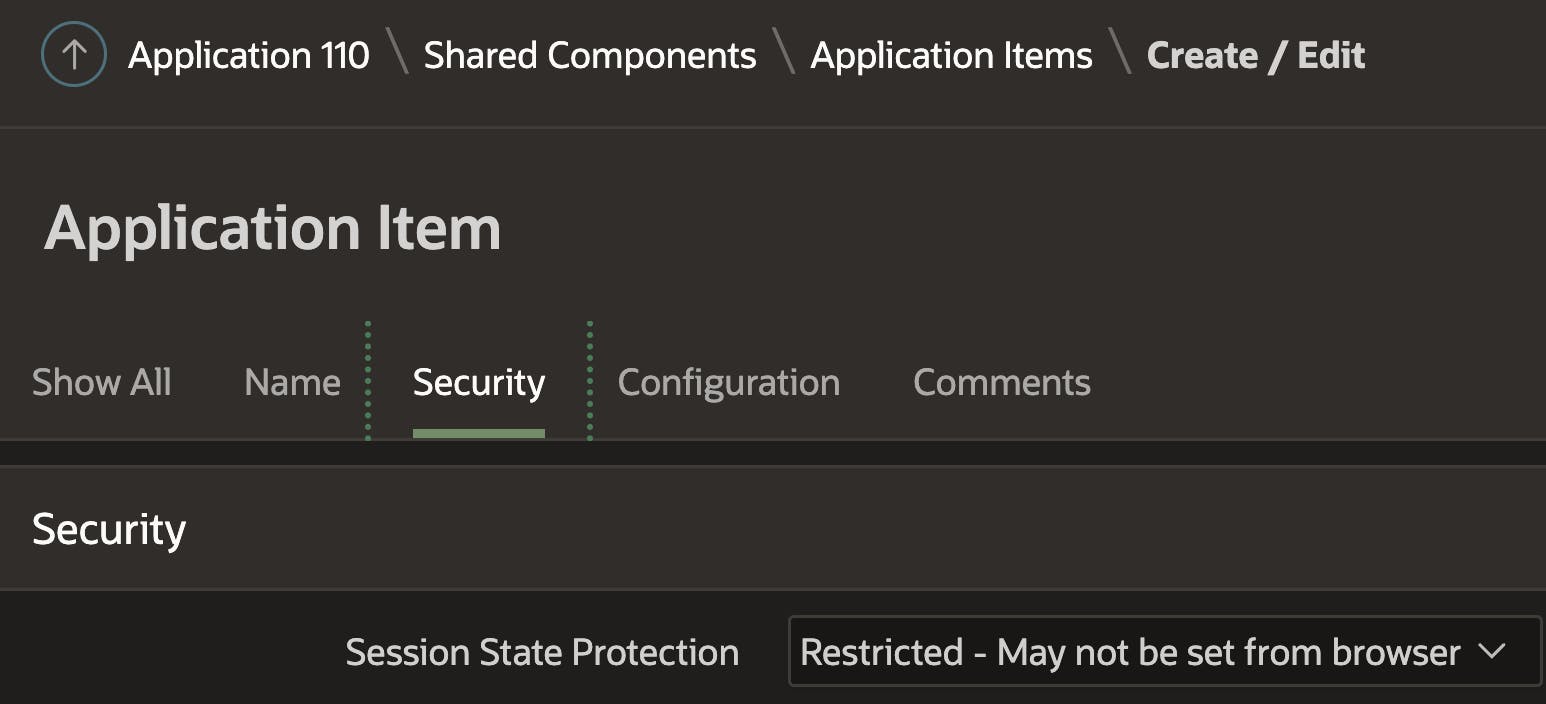
Recommendation
Set to 'Restricted - May not be set from browser' unless you have a specific reason not to.
Exceptions to the Rule
There are some scenarios where you may have to disable SSP for an application or page item, but they are few and far between. If you need to disable SSP for a page item, make sure you have a good reason. Add code to defend against malicious updates to the item's value when necessary.
Useful Queries
You can use the following queries to check for pages, page items, and application items at risk from URL Tampering.
Unprotected Pages
SELECT workspace
, application_id
, page_id
, page_name
FROM apex_application_pages
WHERE page_access_protection = 'Unrestricted'
Unprotected Page Items
SELECT workspace
, application_id
, page_id
, page_name
, item_name
, item_protection_level
FROM apex_application_page_items
WHERE item_protection_level = 'Unrestricted'
ORDER BY workspace
, application_id
, page_id;
Unprotected Application Items
SELECT workspace
, application_id
, item_name
, CASE session_state_protection
WHEN 'B' THEN 'Checksum Required - Application Level'
WHEN 'I' THEN 'Restricted - May not be set from browser'
WHEN 'N' THEN 'Unrestricted'
WHEN 'P' THEN 'Checksum Required - User Level'
WHEN 'S' THEN 'Checksum Required - Session Level'
END ssp_value
FROM apex_application_items
WHERE session_state_protection = 'N';
🔗 Read More
- 🩳 APEX Shorts
- #️⃣ APEX Posts
- 📺 Scott Spendolini's APEX Security Checklist presentation from April 2020 (4 Minutes 50 Seconds in)

